 By Robert Buccigrossi, TCG CTO
By Robert Buccigrossi, TCG CTO
OpenVAS is a system vulnerability scanner that checks visible ports, services it can access for known exploits, and high level web threats (like cross-site script vulnerabilities and improper file access). The TCG Tech Team uses it to periodically scan our gateway machines and websites that we house in our VMWare Workstation lab. OpenVAS is available as part of the Kali Linux distribution, as Ubuntu and CentOS packages, and even as a stand-alone docker image.
Recently, Amazon Web Services (AWS) changed its policy to allow users to conduct vulnerability and penetration testing on EC2 machines without prior authorization, so I used OpenVAS’s “full and fast” scan against TCG’s own website on AWS. It took almost 23 hours to complete! Because our website is configured to give every article its own full URL (for search engine optimization), OpenVAS treated every article as its own directory for CGI-script testing (with over 6000 web vulnerability tests).
When I removed the web vulnerability tests, OpenVAS scanned the site in 8 minutes, but missed a number of potential medium-risk items. I wanted to balance accuracy with duration. As it turns out, I could create a new “full and fast” scan that stayed at the top directory for its CGI-script vulnerability tests. This new “full and fast 1 directory deep” test only took 2 hours and had the exact same findings as the longer test. For significant site updates, I would still do the longer “full and fast”, but the “full and fast 1 directory deep” test is a great way to quickly verify threat mitigations and check top-level system changes.
How to Create a 1‑Directory-Deep Scan: In order to configure the OpenVAS scanner to do 1‑directory-deep CGI-script vulnerability testing, set the regular expression pattern used to exclude CGI directories to /[^/].* . This pattern allows the root directory “/” to be searched, but excludes any other directory. (Specifically, this pattern excludes any path that begins with a slash followed by a non-slash character.) To implement this change:
1) In the Greenbone Security Assistant, use the “Configuration” → “Scan Configs” menu to list the various scan configurations.
2) Find “Full and fast” and click the sheep icon (“Clone”):
![]()
3) In the resulting “Full and fast Clone 1” configuration, click the wrench to edit it:

4) In the resulting dialog box, feel free to rename the config, but more importantly, find and click the wrench next to “Regex pattern to exclude directories from CGI scanning”:
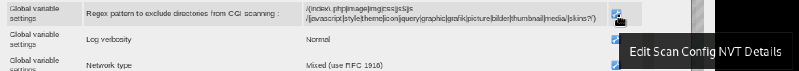
5) In the resulting popup, set “Regex pattern to exclude directories from CGI scanning” to /[^/].*
6) Click “Save” to save and close the pop-up configuration screens
To scan 2 directories deep, change the regex pattern to /[^/][^/]*/[^/].* . (This excludes any path that begins with two slashes separated by at least one non-slash character.)
This is not a rigorous as the regular “full and fast” scan, but is great for a quick tune-up scan, and I hope saves you time.